Picture this: it’s 2007. A very wealthy prince desperately wants to gift you a portion of his inheritance. But you (heartless you) ignore him, moving his email to your spam folder. Fast forward a couple of years, and the prince has changed. Our prince goes by a new name now, maybe Microsoft Outlook, Dropbox, or perhaps your very own employer. This time our ‘friend’ has no fortune to give, but your data is still on his mind.
A key aspect of phishing training at SPS Commerce is Phishing Awareness Campaigns. These campaigns simulate popular phishing practices as they evolve. This information is used to make future phishing simulations that reinforce positive phishing behaviors around topics our employee base has underperformed with in the past.
Malicious actors like our Prince Poser have advanced since the days of blatant misspellings and promises of free cruises. Now, phishes come in the form of professional-looking emails scraped directly from real business sites and correspondences. As phishes become more realistic, we SPSers must learn the new ways to spot them.
Fish in the Sea
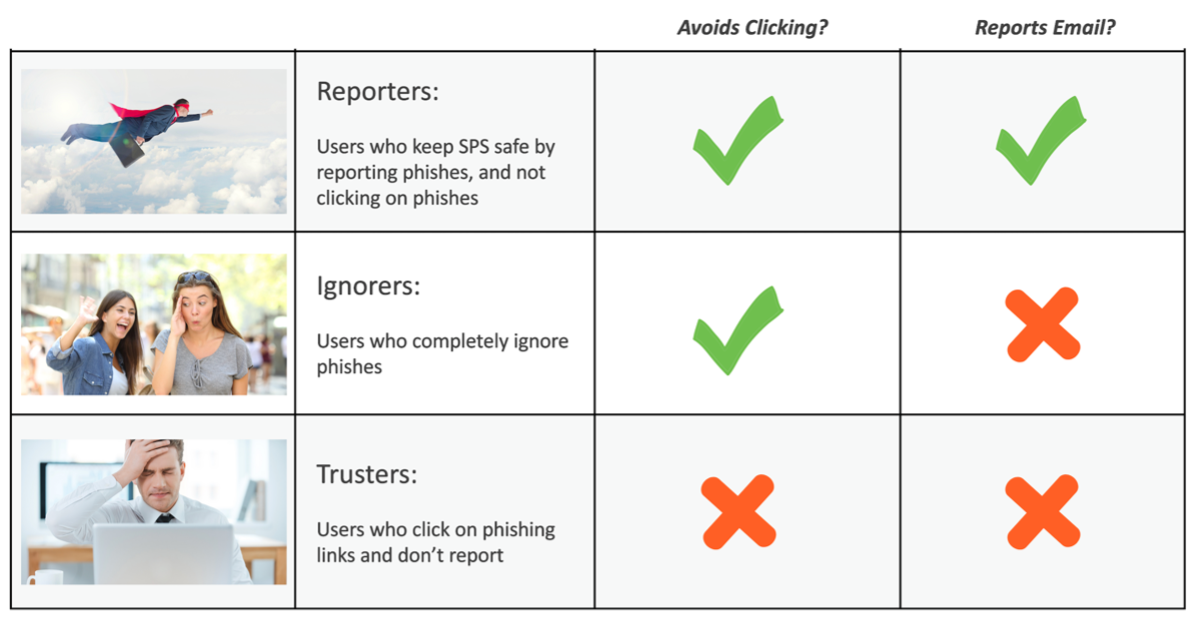
In phishing campaigns, there are three broad categories of users. At SPS, we use this categorization to understand our phishing posture across the organization. The goal of phishing awareness campaigns is to create an organization full of reporters who actively protect the employee base from attacks. But how do Reporters do it? What makes them so astounding and email-savvy? It’s simple: they know the tactics of influence that phishers use in their fraudulent messages.
Phish Bait
Next, we discuss notable themes that phishers use to manipulate users and how these themes look in your inbox. We use these themes to categorize phishing simulations at SPS and to cater them to SPS’s needs. Examine the example phishing email below and see how many red flags you catch.
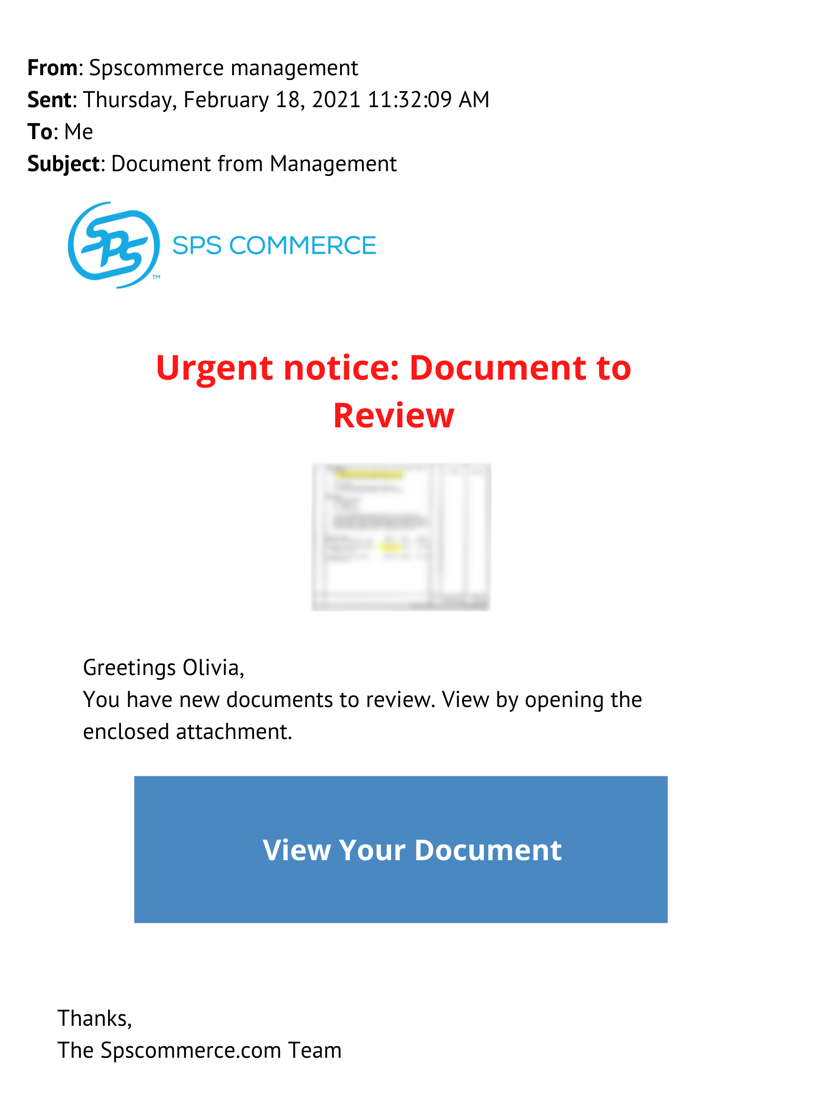
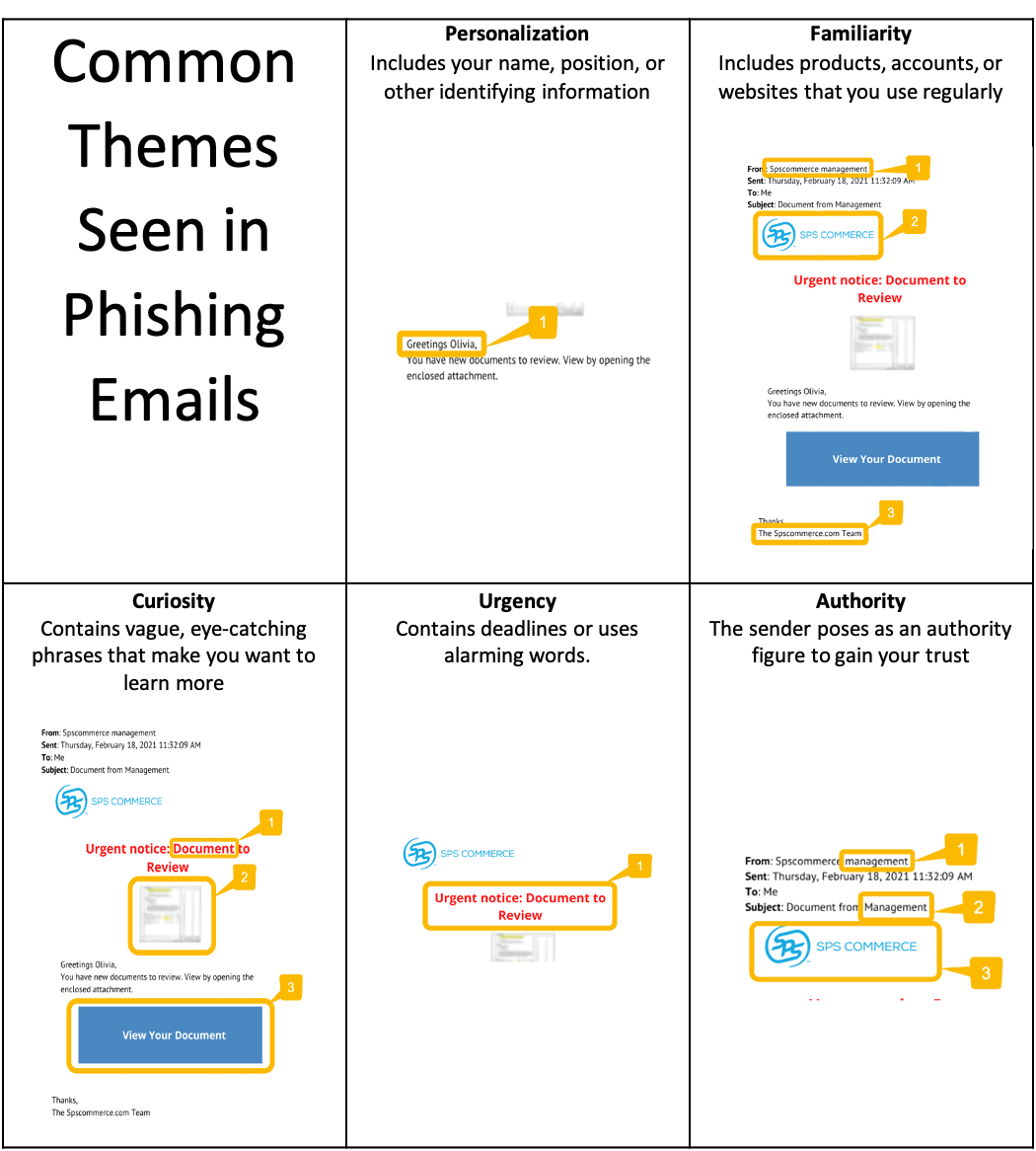
Gone are the days of obvious typos and promises of free trips. The themes below show up regularly in modern phishing emails, so the next time you get a suspicious email, ask yourself if the sender may be using any of the following tactics to “hook” you.
Phishing Program in Action
The SPS phishing program caters phishing simulations towards what our users need. Our goal is to make our “Trusters” stop trusting, and our “Ignorers” report phishes. We analyze past data to find what themes our users are most susceptible to, then craft elements of our phishing simulations that specifically cater to those themes. By doing this, our Trusters will gradually become accustomed to distrusting suspicious emails that they used to be fooled by.
What users see when they click on a phishing simulation link is even more important than the phish itself. An amiable yet informative landing page is key to getting users to rectify their mistake. Our landing pages use typical SPS design formatting and point out specific details from each phish that were suspicious. Our landing page stresses comradery, not isolation; we are all on the same side when it comes to phishing attacks.
After putting data-driven phishing themes and encouraging landing pages into practice, we’ve noticed significantly higher reporting levels and lower click rates from our end users.
Get “Betta” at Phish Detection
Awareness is the key step to detecting phishing. The next time you get an unexpected email, ask yourself if the sender might be using the tactics above to try to “social engineer” you. Here are some other great tips:

SPS maintains a “defense in depth” security posture with multiple technical controls; SPS employees are the last line of defense against phishing emails. SPS Security implements these data-driven phishing simulations to keep employees, customers, and SPS data safe in a dynamic phishing landscape.
Want to learn more about phish detection? Try these great articles (but hover over the links first 😉)!
- Phishing Prevention Tips, Kaspersky Lab
- How to Recognize and Avoid Phishing Scams, U.S. Federal Trade Commission
- Spam and Phishing, National Cybersecurity Alliance
- The Anatomy of a Phishing Email,
Varonis